What’s the Role of a Chief Information Security Officer?
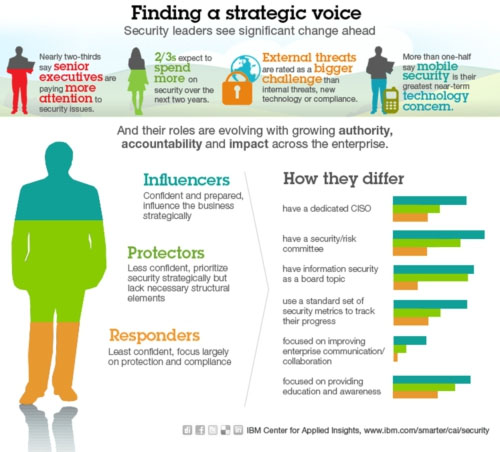
In a study, nearly two-thirds of Chief Information Security Officers (CISOs) surveyed say their senior executives are paying more attention to security today than they were two years ago, with a series of high-profile hacking and data breaches convincing them of the key role that security has to play in the modern enterprise.
More than half of respondents cited mobile security as a primary technology concern over the next two years. Nearly two-thirds of respondents expect information security spend to increase over the next two years and of those, 87 percent expect double-digit increases.
Overall, the study says, all security leaders today are under intense pressure, charged with protecting some of their firm’s most valuable assets – money, customer data, intellectual property and brand.
[ Also Read: Seven Critical Tips to Stay Safe in the Cyberspace ]The IBM (NYSE: IBM) study reveals a clear evolution in information security organizations and their leaders with 25 percent of security chiefs surveyed shifting from a technology focus to strategic business leadership role.
In IBM’s first study of senior security executives, its Center for Applied Insights interviewed more than 130 security leaders globally and discovered three types of leaders based on breach preparedness and overall security maturity.
Representing about a quarter of those interviewed, the “Influencer” senior security executives typically influenced business strategies of their firms and were more confident and prepared than their peers—the “Protectors” and “Responders.”
[ Also Read: How Asian Companies Address Security Threats ]Rather than just reactively responding to security incidents, the CISO’s role is shifting more towards intelligent and holistic risk management – from fire-fighting to anticipating and mitigating fires before they start.
“This data painted a profile of a new class of CISO leaders who are developing a strategic voice, and paving the way to a more proactive and integrated stance on information security,” said David Jarvis, author of the report and senior consultant at the IBM Center for Applied Insights.
“We see the path of the CISO is now maturing in a similar pattern to the CFO from the 1970s, the CIO from the 1980s – from a technical one to a strategic business enabler. This demonstrates how integral IT security has become to organizations.”
To create a more confident and capable security organization, IBM recognizes that security leaders must construct an action plan based on their current capabilities and most pressing needs. The report offers prescriptive advice from its findings on how organizations can move forward based on their current maturity level.
[ Also Read: Are Workers Unaware of IT Security Policies? ]For example, those “Responders” in the earliest stage of security maturity can move beyond their tactical focus by establishing a dedicated security leadership role (like a CISO); assembling a security and risk committee measuring progress; and automating routine security processes to devote more time and resources to security innovation.
The IBM Center for Applied Insights study, “Finding a strategic voice: Insights from the 2012 IBM Chief Information Security Officer Assessment,” included organizations spanning a broad range of industries and seven countries.
During the first quarter of 2012, the Center conducted double-blind interviews with 138 senior business and IT executives responsible for information security in their enterprises. Nearly 20 percent of the respondents lead information security in enterprises with more than 10,000 employees; 55 percent are in enterprises with 1,000 to 9,999 employees. The findings of the study were released today, May 3.