Global organizations are more confident than ever that they can predict and resist a sophisticated cyber attack.
But they are falling short of investments and plans to recover from a breach in today’s expanding threat landscape, according to the annual EY Global Information Security Survey (GISS), Path to cyber resilience: Sense, resist, react.
Now in its 19th year, the survey of 1,735 organizations globally examines some of the most compelling cybersecurity issues facing businesses today in the digital ecosystem. The survey findings were released Tuesday.
Findings showed that half (50%) of those surveyed said they could detect a sophisticated cyber attack – the highest level of confidence since 2013.
This is due to investments in cyber threat intelligence to predict what they can expect from an attack, continuous monitoring mechanisms, security operations centers (SOCs) and active defense mechanisms.
However, despite these investments, 86% of those surveyed say their cybersecurity function does not fully meet their organization’s needs.
Nearly two-thirds (64%) of organizations do not have a formal threat intelligence program or have only an informal one. When it comes to identifying vulnerabilities, more than half (55%) do not have vulnerability identification capabilities or only have informal capabilities, and 44% do not have a SOC to continuously monitor for cyber attacks.

When asked about recent significant cybersecurity incidents, more than half (57%) of respondents said they had an incident. Nearly half (48%) cited outdated information security controls or architecture as their highest vulnerability – an increase from 34% in the 2015 survey.
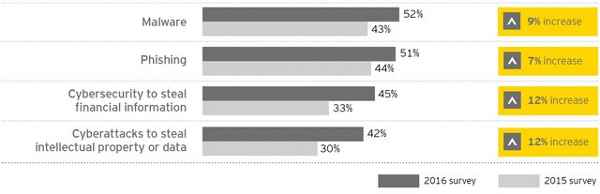
In addition, respondents said all of their top cybersecurity threats, including malware, phishing, cybersecurity to steal financial information, or cyber attacks to steal intellectual property or data are on the rise.
Business continuity and disaster recovery – which is at the heart of an organization’s ability to react to an attack – was rated by respondents as their top priority (57%), along with data leakage and data loss prevention (57%).
Although 42% plan to spend more this year on data leakage and loss prevention, only 39% plan to spend more on business continuity and disaster recovery.
This year’s survey also shows that respondents continue to cite the same key areas of concern for their cybersecurity, such as the increased risks from the actions of careless or unaware employees (55% compared with 44% in 2015) and unauthorized access to data (54% compared with 32% in 2015). Meanwhile, obstacles to their information security function are virtually unchanged from last year, including:
- Budget constraints (61% compared with 62% in 2015)
- Lack of skilled resources (56% compared with 57% in 2015)
- Lack of executive awareness or support (32%, the same as in 2015)
Despite the connected nature of today’s digital ecosystem, the survey found that 62% of global organizations said it was unlikely they would increase their cybersecurity spending after a breach that did not appear to do any harm to their operations.
Also, 58% said it was unlikely they would increase their information security spending if a competitor was attacked, while 68% said it was unlikely they would increase their information security spending if a supplier was attacked.
In the event of an attack that definitely compromised data almost half of the respondents (48%) would not notify customers who had been impacted within the first week. Overall, 42% of respondents do not have an agreed communications strategy or plan in place in the event of a significant attack.
When it comes to devices, organizations are struggling with the number of devices that are continuously being added to their digital ecosystem. Almost three-quarters (73%) of organizations surveyed are concerned about poor user awareness and behavior around mobile devices, such as laptops, tablets and smartphones. Half (50%) cited the loss of a smart device as a top risk associated with the growing use of mobile devices because they encompass both information and identity loss.






